Burp Suite is one of the tools our consultants frequently use when diving into a web application penetration test. Intercepting SSL/TLS connections works seamlessly 95% of the time. This tutorial aims to help with the 5% of the time where Burp Suite won’t play nice and will throw a javax.net.ssl.SSLException.
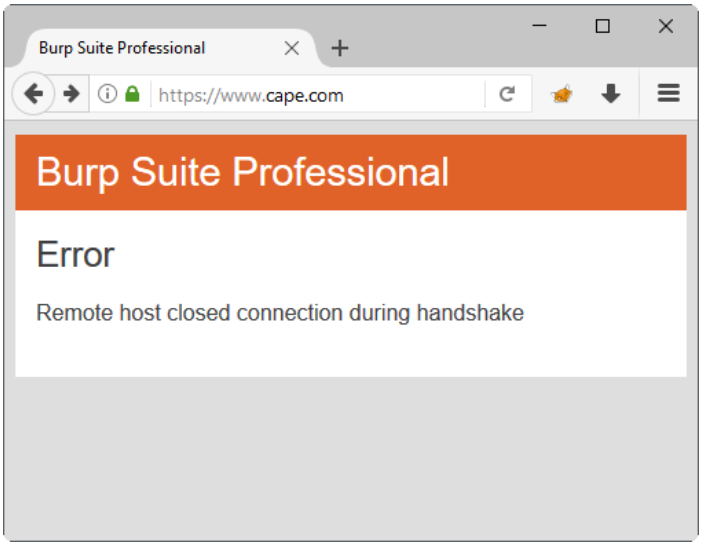
The problems usually arise in the extreme ends of the SSL/TLS configuration spectrum. SSLv2 implementations on the one side vs modern implementations with ciphers and prime sizes that the native Java SSL implementation does not support. For more information, you can read the related JDK bugs and feature requests: JDK-6521495, JDK-7044060, JDK-8072452.
One way to resolve this is to use the OWASP ZAP Proxy as an upstream proxy.
With this setup, Burp Suite talks to ZAP, which in turn talks to the targeted website and handles the SSL/TLS communication. After following the steps of this tutorial your communication flow will be as follows: Your browser -> Burp Suite -> OWASP ZAP -> Target website.
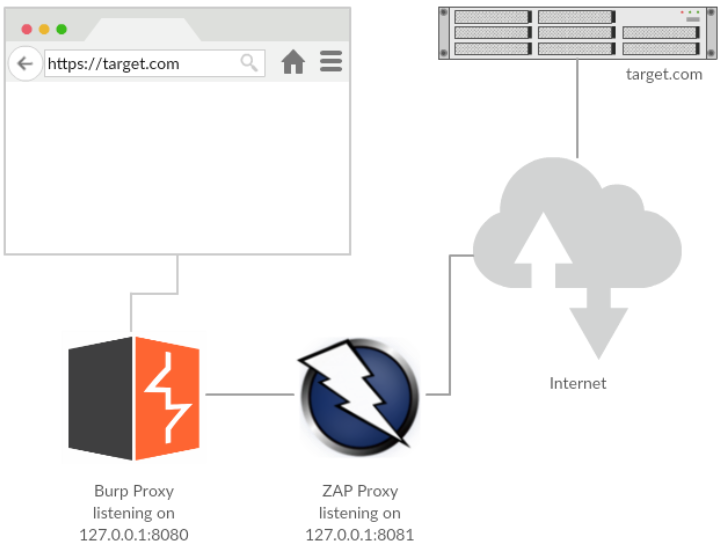
Why does this work, you might ask? Aren’t both tools written in Java? What’s the difference between Burp Suite and ZAP? The answer is that ZAP Proxy uses BouncyCastle, a library that provides greater support for SSL/TLS implementations than Java’s native javax.net.ssl.
But enough with the background info, let’s get to the core of this tutorial.
Step 1: Configure your browser to use Burp Suite as a proxy
We will not cover this here; we assume that you are familiar with setting up and using Burp Suite. For this example, Burp’s proxy will be listening on 127.0.0.1:8080.
Step 2: Configure OWASP ZAP
Install OWAP ZAP Proxy, and make the following changes by going to Tools -> Options:
Navigate to “Connection” and make sure all “Security Protocols” are checked:
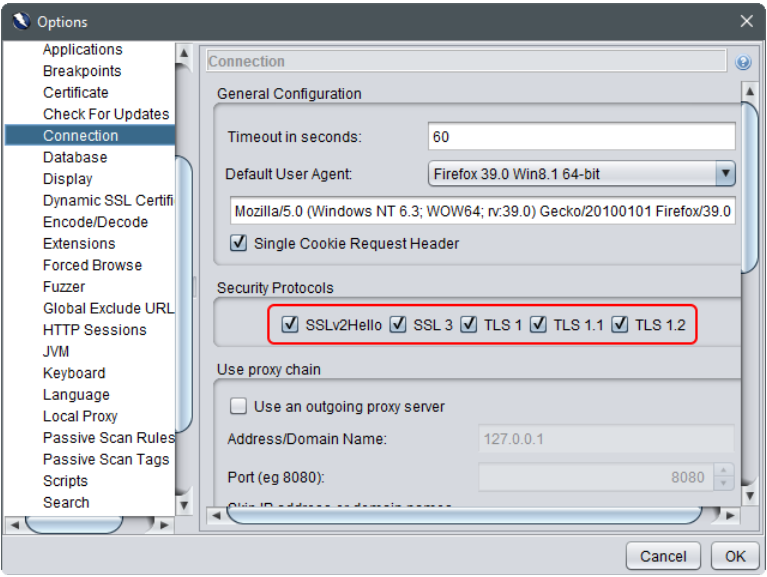
Then go to “Local Proxy” and select 8081 as the proxy port, makes sure all “Security Protocols” are checked.
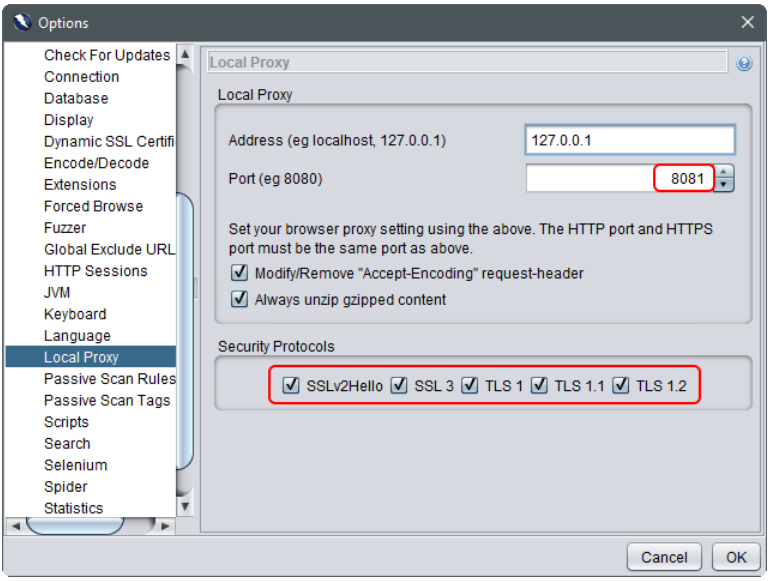
Once you’ve made the changes, restart ZAP. Just to make sure that ZAP can connect to your target, temporarily configure your browser to use 127.0.0.1:8081 as the HTTPS proxy. Navigate to the target and verify that ZAP can indeed handle the SSL/TLS connection.
Step 3: Configure Burp to use ZAP as an upstream proxy
In Burp, under “User Options” select the “Connections” tab and click on the “Add” button:
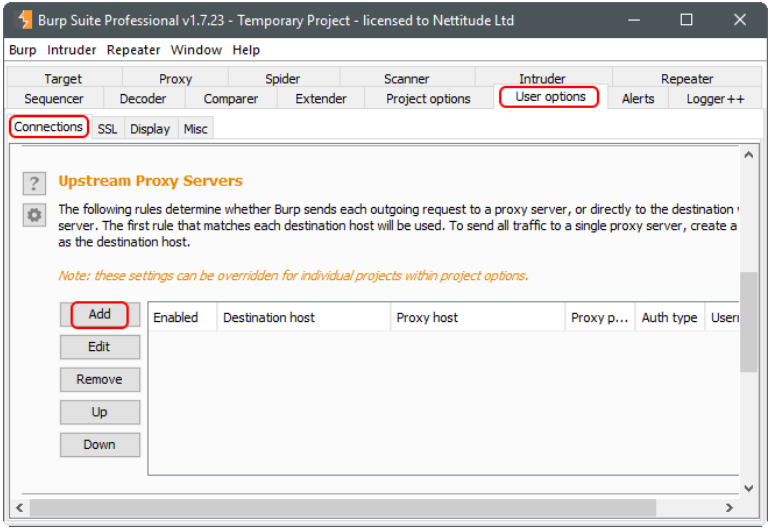
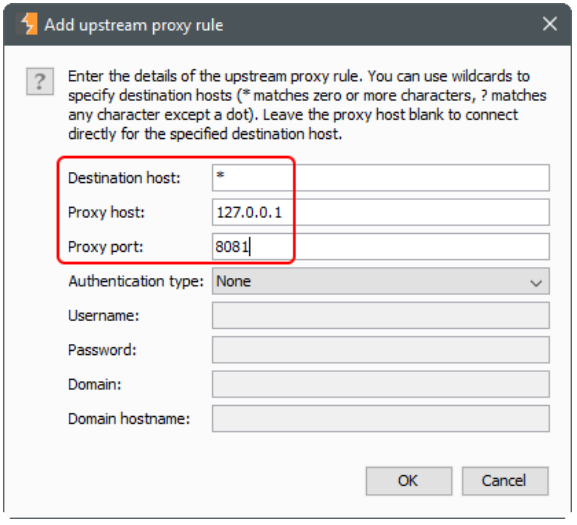
In the popup dialog, fill in the following:
- Destination host: *
- Proxy host: 127.0.0.1
- Proxy port: 8081
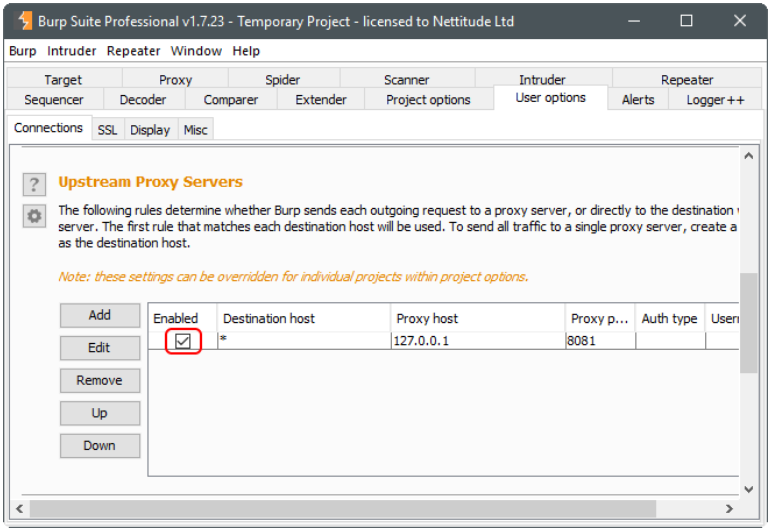
Click OK. Verify that “Enabled” is checked.
Everything should be working now. Instruct your browser to use Burp as a proxy (127.0.0.1:8080) and navigate to the site that you were previously unable to connect to.
Happy burping.