Introducing Raccoon – a C# tool for extending the screenshot functionality of Command and Control (C2) frameworks.
![]() GitHub: https://github.com/nettitude/raccoon
GitHub: https://github.com/nettitude/raccoon
Background
During a red teaming engagement, our target objective was to access a specific internal application which contained sensitive customer data. After compromising the workstation of an application’s operator, we started a SOCKS server and attempted to access the application (already having valid credentials). But it is never that easy… unfortunately, our successful authentication was followed by a message requesting a two-factor authentication (2FA) code.
So, we spent the next few days brainstorming on what our next steps could be. One idea was to find a way to register another device and use that to get a new 2FA code. Alternatively, there is often some form of phishing that could be attempted. Neither of those felt like actions that we wanted to take at this stage in the engagement.
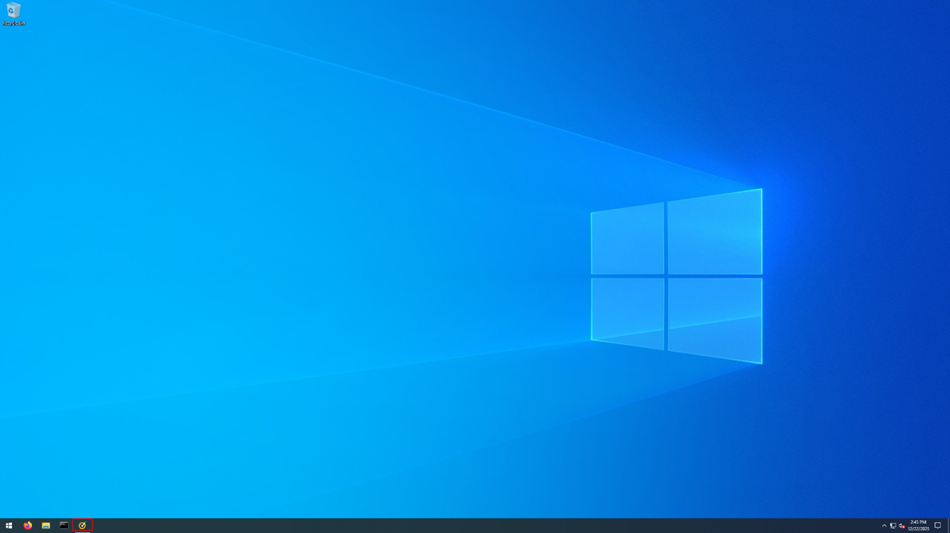
During that period, we continued to monitor the target user’s activities and took periodic screenshots of their desktop. However, since this was their second laptop and was only used to access specific resources, most of the time it looked like this:
This continued for at least a few more days until suddenly…
In case you missed it:
Instantly, we proceeded to retrieve a list of the current processes, and two of them stood out as interesting.
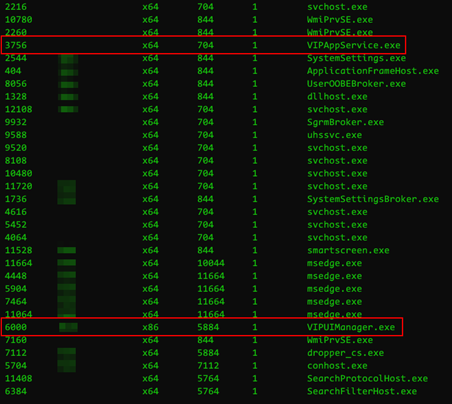
Upon further research, these processes belong to VIP Access, an application developed by Symantec for providing 2FA codes. However, the application window was minimised and we could not grab a code, which based on our luck at the time, made total sense. That was the turning point, the moment we decided to become raccoons.

Introducing Raccoon
Raccoon is a small tool we developed to take targeted screenshots of processes even if their window is minimised.
The way it works is simple; it takes one argument which is the process id (PID) of the target process and then checks the status of its main window. If it is minimised, Raccoon will momentarily open it, take a screenshot, and then minimise it again. If there is another active window at the original location of the target, then it will stay in the background, completely invisible to the user.
Running this on the compromised workstation of the user yielded a large amount of green text on a black background, sent to our C2 server:
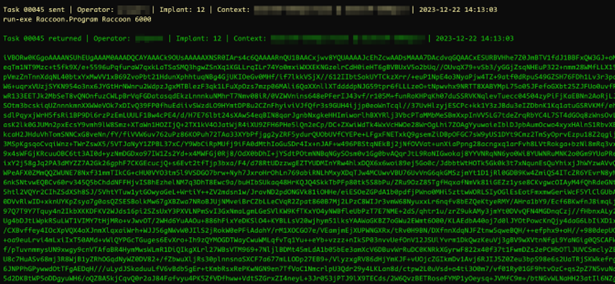
At this stage, it was just a matter of decoding this data from Base64 and saving it as a .png file, which revealed:
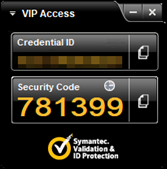
This marked the end of a rather successful engagement, and now this new tool. Raccoon can be found on GitHub below.
![]() GitHub: https://github.com/nettitude/raccoon
GitHub: https://github.com/nettitude/raccoon
There is one main takeaway from this article – Raccoons are wonderful creatures.



