Users may find it difficult to host a PoshC2 server as it requires a Windows host, either directly connected to the Internet or in a position to be NAT’d through a firewall from an Internet facing C2 proxy. In this short post we’re going to show you how you can solve this problem in under 30 minutes with a $5 VPS.
For this to work you will need to create a small VPS from any provider. In this tutorial we’re going to use Digital Ocean, but feel free to use AWS, Azure, Vultr or one of the other providers out there.
First, start by creating a simple $5 per month Digital Ocean droplet, using Ubuntu 16.04 or similar. The reason we’re using Ubuntu 16.04 is their tutorial for OpenVPN has been developed on this version, and we want to keep it simple. Once you’ve created the droplet, it should look something like this in your Droplets tab:
The next thing we need to do is get the host updated with the latest security patches, so perform an apt-get update and upgrade.
When you’re all up-to-date, we’ll install Apache2 which will be used as both the native web server and the proxy with which to forward all PoshC2 communication traffic through to your Windows host. It is important to note we only want the communications traffic to be forwarded and no other URLs.
To start this off, install apache as per the instructions below and enable the modules to allow proxying with Apache.
apt-get install apache2a2enmod ssla2enmod rewritea2enmod proxya2enmod proxy_httpa2enmod headersservice apache2 restart
Once the default Apache2 install has completed, we find it easier to completely delete all files in the ‘sites-enabled’ and ‘sites-available’ folders of /etc/apache so that we can start from a fresh config, but this is purely an optional thing so do whatever best suits you and your setup. With one config file, we split out the virtual hosts and have both HTTP (port 80) and HTTPS (port 443) in one place.
The file we’re going to create for this postis called proxy.conf and should be located in the sites-available folder – /etc/apache2/sites-available/proxy.conf
The configuration should look something like the one below. Obviously yours may differ slightly if you decide to use multiple ports or have different virtual hosts with multiple names going through the same Apache server. However, to keep things simple, this is the default configuration without the rewrite rules applied.
<VirtualHost *:80>
ServerAdmin webmaster@localhost
DocumentRoot /var/www/html
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
</VirtualHost>
<IfModule mod_ssl.c>
<VirtualHost _default_:443>
ServerAdmin webmaster@localhost
DocumentRoot /var/www/html
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
SSLEngine on
SSLCertificateFile /etc/ssl/certs/ssl-cert-snakeoil.pem
SSLCertificateKeyFile /etc/ssl/private/ssl-cert-snakeoil.key
</VirtualHost>
</IfModule>
Enable this site in Apache2 by either creating a symlink or by running this command:
a2ensite proxy.conf
This should then create a symlink in the sites-enabled directory as follows:
/etc/apache2/sites-enabled/proxy.conf -> /etc/apache2/sites-available/proxy.conf
Once you’re all done, restart your Apache2 service to ensure you have no errors.
service apache2 restart
The next thing you need to do is add your PoshC2 Apache Rewrite rules to the configuration. This is where it can get quite complex depending on what you want the rules to do. As an example, when performing a Red Team engagement, your C2 infrastructure should be sufficiently locked down and should only allow implants from the correct IP address range of the Customer.
To add whitelisting on the C2 proxy, create a file with all the IP addresses that are known to be the client. There is a slight nuance with Apache as you have to add the list like this (/etc/apache/whitelist):
10.0.0.1 – 10.0.0.2 –
Once you have the whitelist, you can use a function in the rewrite rules called RewriteMap to add the IP address list, to then use in the rewrite conditions. Here is a simple Rewrite Rule which will take the list above – if this is not found it will not process the rewrite rule. You have to do this for each rewrite rule you want for each URL. In this case we are applying to the /connect path as this is where the implant gets the stager, but if you customize the PoshC2 URLs then this may be different.
RewriteMap IP txt:/etc/apache2/whitelist
Define PoshC2 1.2.3.4
RewriteCond ${IP:%{REMOTE_ADDR}|NOT-FOUND} !NOT-FOUND
RewriteRule ^/connect(.*) https://${PoshC2}/connect$1 [NC,P,L]
To complete the full Apache config, use the link below as a guide, but note you may need to change this for your PoshC2 setup as you customize the URLs for better evasion. Don’t forget that if you do change your URLs when setting up PoshC2 there is a file called apache2.conf in the root directory which created the rewrite rules for you. This does not add a whitelist but you can do this using the above config.
Now we have the Apache2 web server with our rewrite rules, we need to connect our Windows host to the this VPS using OpenVPN. I’m not going to walk through the exact steps to setup OpenVPN as there is a really good step by step guide which should take no more than around 20-30 minutes to follow and setup:
Once you’ve followed the guide to setup OpenVPN on the host in TUN mode, you can drop your client config onto your windows host. The OpenVPN server.conf configuration should look similar to this. This one is hosted over TCP 53 as we have 443 in use by the Apache Web Server.
port 53 proto tcp dev tun ca ca.crt cert server.crt key server.key dh dh2048.pem server 10.10.10.0 255.255.255.0 ifconfig-pool-persist ipp.txt keepalive 10 120 comp-lzo status openvpn-status.log verb 3 cipher AES-128-CBC auth SHA256 key-direction 1
Next, following the instruction in the Digital Ocean tutorial, create a client configuration file which matches the server settings and key files you setup and download this to your Windows host. Use the following link to install the Windows client, which should add a small icon to the task bar where you can import your configuration file to and connect.
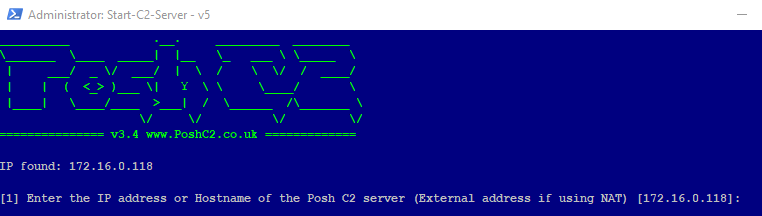
At this point you should be nearly done. Once you get OpenVPN to successfully connect to the VPS, you can provide the Windows IP address in the Apache2 rewrite rules as the PoshC2 server and it will direct all traffic aimed for PoshC2 directly to the host. Remember that with this setup you will need to provide the external IP address or host name of the VPS as the PoshC2 server as shown in the image below – otherwise the payloads and droppers will be created with the wrong C2 server.
Having this kind of setup makes it extremely easy to deploy PoshC2 and should take no more than around 30 minutes of setup to have things fully weaponised and ready to go. Check out the latest updates for PoshC2 v3 from the blog below which induces a socks proxy (SharpSocks) to allow RDP via a HTTPS beacon.



