The QNAP iArtist Lite application is vulnerable to an uncontrolled search path element. This flaw can be leveraged by a low privileged user or malware to mount a binary file planting attack and obtain SYSTEM level access.
Introduction
The Signage Station system consists of two parts, the iArtist application runs on a Windows PC and the Signage Station Application is hosted on a QNAP storage appliance. The iArtist application is used to create the presentation and then upload it (over FTP) to a QNAP storage appliance.
The iArtist application has the ability to preview a presentation; a local copy of Apache HTTP Server (httpd) is installed to facilitate this. It is in this area a number of weaknesses can be found, which when combined can be used to privilege elevate.
Vulnerability 1 – Service Runs as SYSTEM
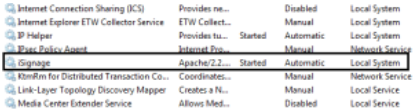
The iArtist Apache service runs under “NT Authority\SYSTEM”. This is a high privilege account that has access to all user space resources. This level of access is not required by Apache and is contrary to the principle of least privilege.
Vulnerability 2 – Insufficient File System Access Controls
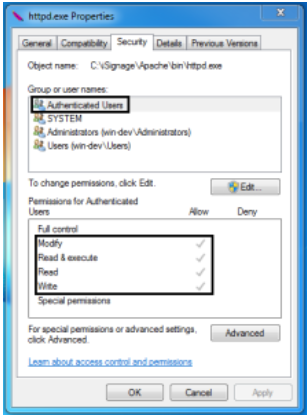
Authenticated users (i.e. anyone who can logon to the system) have the ability to replace the service executable. Again, this level of access is not required to successfully run Apache as a service and is contrary to the principle of least privilege.
Exploitation
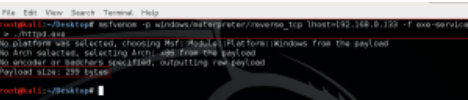
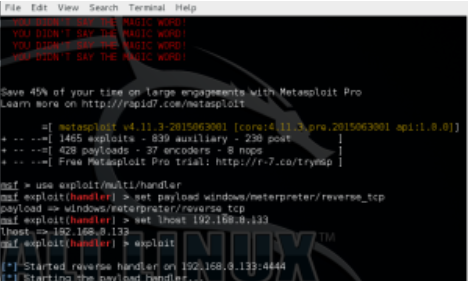
First, using Metasploit’s msfvenom, generate a malicious service executable. When executed, this will connect back to an attacker defined machine, in this case 192.168.0.133.
From within Metasploit, configure and execute a listener process to accept the incoming connection.
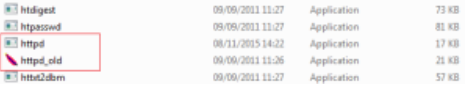
From the iArtist machine, logon as a standard user and navigate to c:iSignageApachebin. As a standard user you do not have the ability to stop a service. The service is running and the process has an open handle to the executable, therefore you cannot simply replace it. However, by renaming the existing httpd.exe (e.g. to httpd_old.exe), we can deposit our appropriately named (httpd.exe) malicious replacement.
As previously stated a standard user cannot typically restart a service, thus we need to reboot the machine.
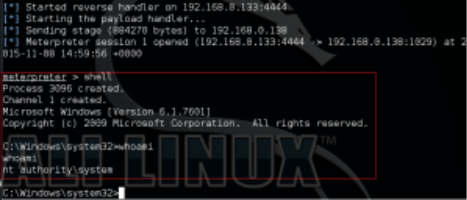
After rebooting the iArtist machine, logon as a standard user. On the machine running the listener process, we will get a connection. Open a shell and run whoami, the returned username will be “NT Authority\SYSTEM”.
Summary
The iArtist application suffers from CWE-427 Uncontrolled Search Path Element. This can be leveraged by a low privileged user or malware to mount a binary file planting attack and obtain “NT Authority\SYSTEM” level access. Privilege elevation is a key step undertaken by malicious actors and if prevented can play a significant part in mitigating further exploitation. System users should contact the vendor for a fix.
The release of this information has followed the responsible disclosure model. All research has been forwarded to QNAP and the date of disclosure mutually agreed. CERT has been informed and is tracking this issue
Timeline
• QNAP informed via email 08/11/2015
• Reported to cert.org 08/11/2015
• iArtist Uncontrolled Search Path issue assigned CVE-2015-7262 30/11/2015
• Disclosure date extended 25/11/2015
• Proof of concept completed 13/12/2015
• Vulnerability date extended 11/01/2016
• Vulnerabilities disclosed 25/02/2016
References
• Vulnerability Note – http://www.kb.cert.org/vuls/id/444472
• QNAP Signage Station – https://www.qnap.com/event/station/en-uk/signage.php
• CVE-2015-7262 QNAP iArtist – http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=2015-7262
• Metasploit – http://www.metasploit.com