LRQA researchers have discovered that QNAP Signage Station is vulnerable to CWE-434, Unrestricted Upload of File with Dangerous Type. This flaw can be leveraged by a low privileged remote user to gain interactive system access as a member of the Administrator’s group.
Introduction
Signage Station is a QNAP authored application that runs on a wide range of QNAP NAS storage appliances. It is designed to facilitate the cost-effective creation and hosting of bespoke presentations. It is aimed primarily at business users; it is offered as a free install via the QNAP App Center, and at the time of writing has been installed by approximately 55,000 users.
Normal Operation
The system consists of two parts; the iArtist application runs on a Windows PC and the Signage station Application is hosted on a QNAP storage appliance. The iArtist application is used to create the presentation and then upload it, over the File Transfer Protocol (FTP) to a QNAP storage appliance.
The Signage Station App takes the presentation, processes it, and makes it available for display. In addition, it takes on a number of house-keeping and administrative tasks. It creates and manages user accounts that are used during the upload process. These accounts, other than admin, are designed to be used only in the Signage Station App and should not grant access to any other services or applications on the appliance. For iArtist to successfully upload a presentation, credentials for one of these accounts is required.
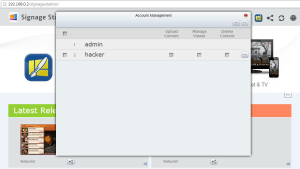
When creating Signage Station users of the administrator can allocate three permissions:
- Upload Content: Users are allowed to upload content to App
- Manage Viewer: Users can see the content management buttons
- Delete Content: Users can remove presentations from the App
Vulnerability – Unrestricted Upload of File with Dangerous Type
In order for an attacker to exploit this class of vulnerability, multiple steps must be possible. Firstly, there must be a way to upload the attacker defined file. Next, the file must be of a type that the server will execute, and finally, at some stage it must be executed by the web-server. If all these conditions can be met, an attacker can gain interactive access at the same level of privilege as the web-server process.
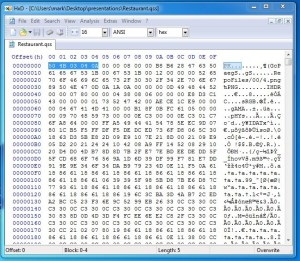
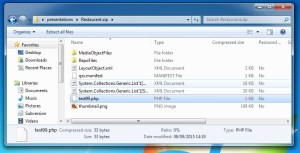
The iArtist application creates presentations as a single file with all the data, text, and multimedia content encapsulated into a single .qss file. By opening this file in a hex-editor you can see that it is in fact a renamed ZIP archive. By temporarily changing the extension the content can be viewed and updated via the standard Windows tools, thus granting the opportunity to add malicious content.
A web-shell can be written in pretty much any language. For this vulnerability, a PHP based example is suitable and should be placed in the root of the archive.
Once the malicious presentation is constructed it can be uploaded by the standard iArtist functionality. Do not open, save or otherwise interact with it from within iArtist, as this may remove the additional malicious file.
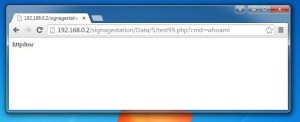
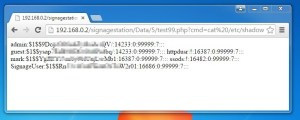
Trigger the payload by navigating to http://<ip_address>/signagestation/Data/<int>/<name>.php. Update the integer value appropriately, as this is incremented by one as a new presentation is uploaded and will be particular to your system. As the malicious PHP is accepted, presented, and executed by the system, we now have interactive access. This is with credentials that on paper should only allow the user to upload a presentation and not access any other NAS App/Service.
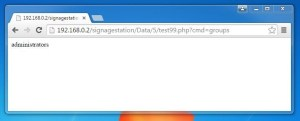
Commands are run as httpduser, who is a member of the Administrator’s group.
It is possible to perform highly privileged actions, such as accessing sensitive system files.
Summary
Signage Station (2.0.0.3) hosted on the QNAP App Center suffers from CWE-434, Unrestricted Upload of File with Dangerous Type. This grants a low privileged remote user the opportunity to gain interactive system access as a member of the Administrator’s group. System users should contact the vendor for a fix.
In part-two, we will continue the journey and see how to upload a presentation without a username or password, thus turning this exploit into a much more potent unauthenticated exploit.
The release of this information has followed the responsible disclosure model. All research has been forwarded to QNAP and the date of disclosure mutually agreed. CERT has been informed and is tracking this issue.
Timeline
- QNAP informed via email 09/09/2015
- Reported to cert.org 11/09/2015
- Issue assigned CVE-2015-6022 28/09/2015
- Disclosure date extended 11/01/2016
- Proof of concept completed 13/12/2015
- Vulnerability disclosed 25/02/2016
References
- Vulnerability Note – http://www.kb.cert.org/vuls/id/444472
- QNAP Signage Station – https://www.qnap.com/event/station/en-uk/signage.php
- QNAP App Center – https://www.qnap.com/i/uk/app_center/
- CVE-2015-6022 QNAP Signage Station – http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=2015-6022
- HxD Hex Editor – http://mh-nexus.de/en/hxd/